This is a write-up for UGGC challenge from NahamCon CTF.
This is an easy web challenge. Once I opened the above URL, I found a simple login page.
After taking a look at the page source I found nothing interesting.
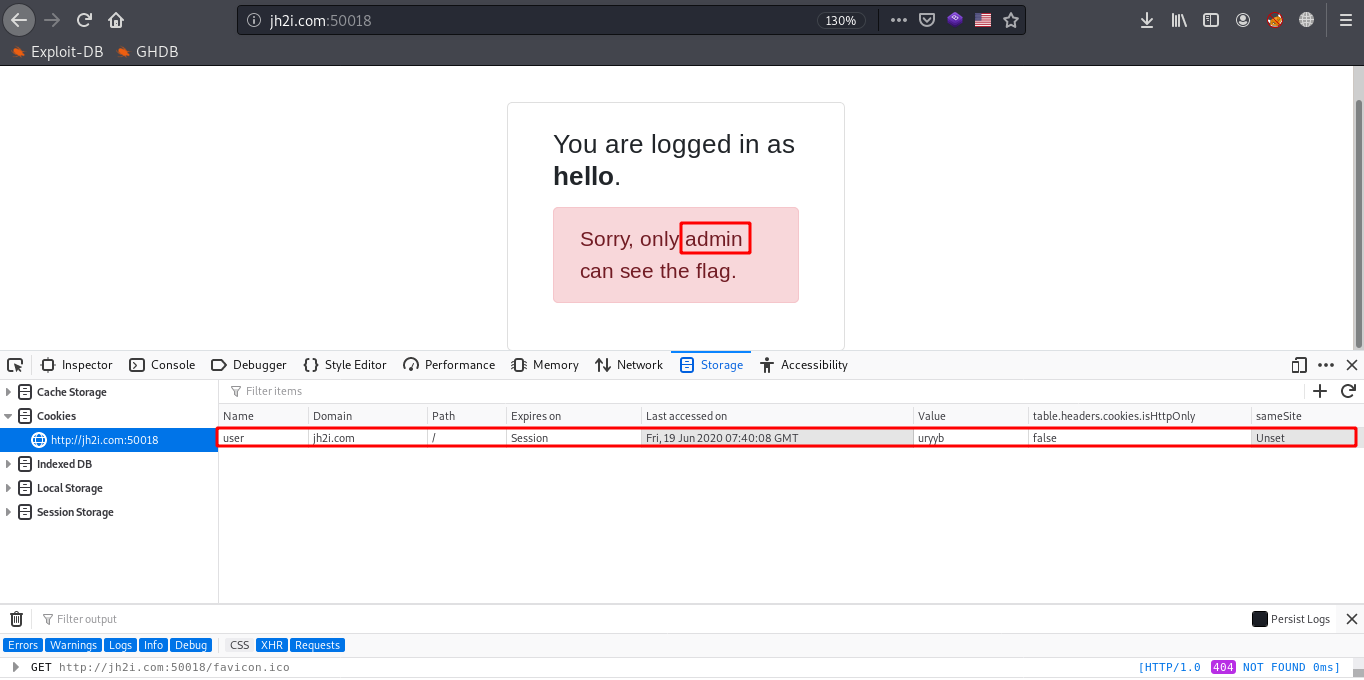
So, lets try to login with any name and see what happens. I entered ‘hello’ as a username and clicked on login, and the response came up with a page saying that only admin can see the flag and a cookie-item named user with value ‘uryyb’.
So, let’s go back again and login with ‘admin’ as a username. After trying to log in with ‘admin’, it responded that login as admin has been disabled!
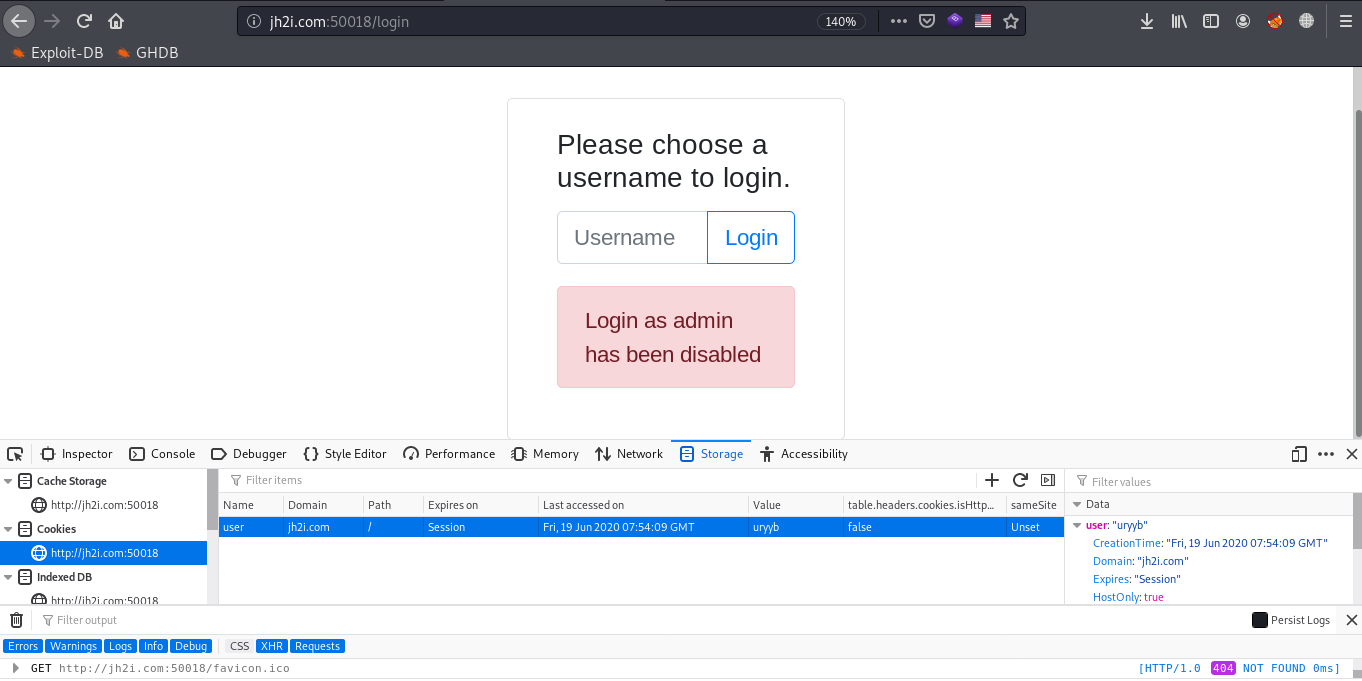
The only thing we have right now is the cookie-item named ‘user’. The value of ‘user’ item is mostly encrypted, so we can take that value and try to decrypt it.
The first thing that came to my mind is that the value is mostly encrypted with ROT13. I tried to decrypt it using https://rot13.com
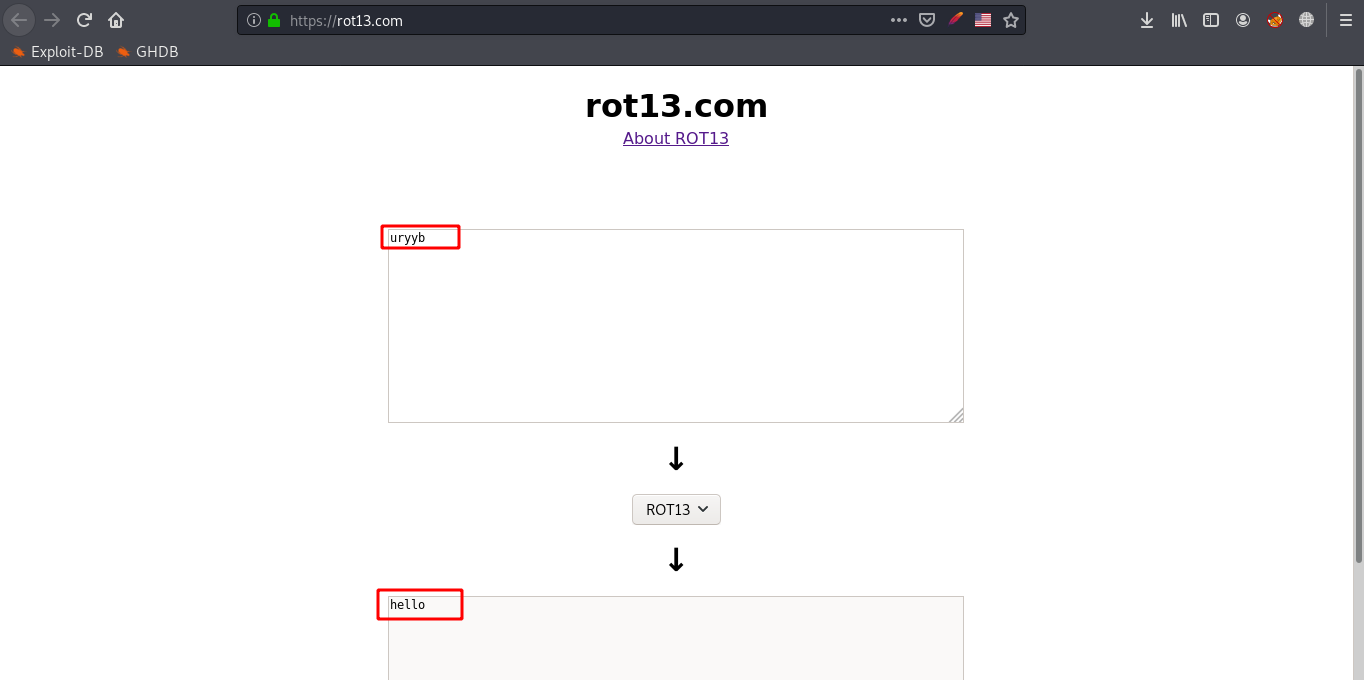
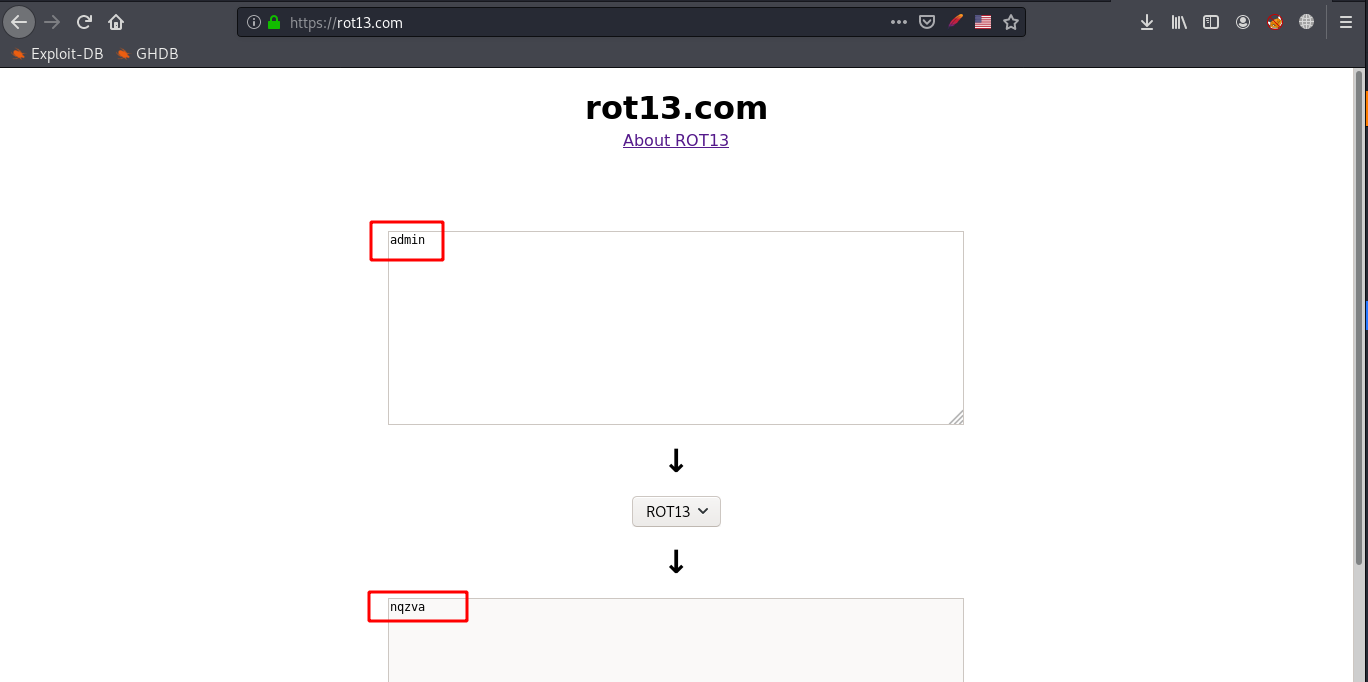
And yes its ROT13 encrypted indeed and the output is ‘hello’ which is the username we tried to log in with before. So lets try to encrypt ‘admin’, Then get the encrypted output and change the value of the cookie-item ‘user’ with the encrypted value of ‘admin’ and resend the request/refresh the page and see what happens.
Yeah, it worked and we finally captured the flag.
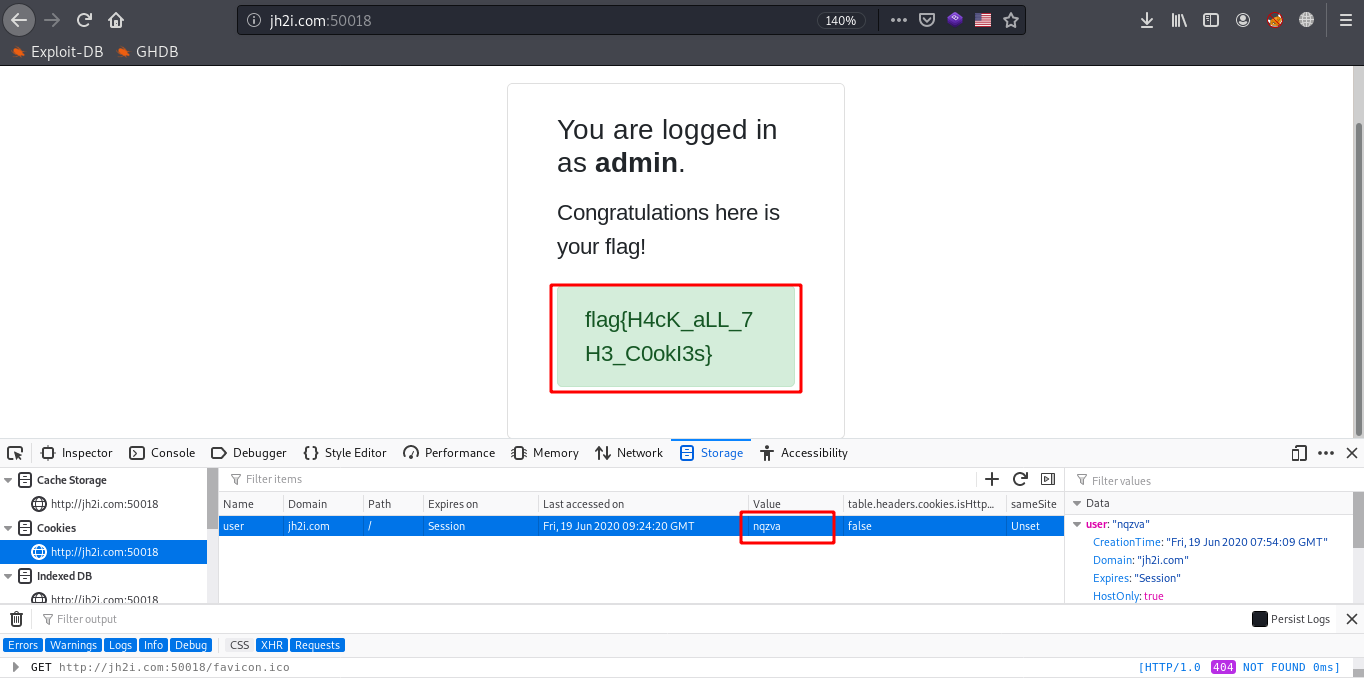
flag{H4cK_aLL_7H3_C0okI3s}